
|
|
|
|
|
|
|
|
|
![]()
For Your Information - Information, Technology, Society
Issue #6, September 25, 2003
It's Not The Technology, Dude™...
1. Microsoft's (In)Security Updates - Blaming the victim for broken software
2. Insidious, malicious email - Be very, very careful
3. Security Catch-22 - Preventing re-infection while downloading patches
4. Personal (In)Security Experience - Letter to the editor
5. State of the attacker's 'art' - Probing your website
6. Security Conclusions - A few (more) things to do to keep your computer safe
7. Voting Systems - Letter to the editor
** Feedback - Comments, please
1. MICROSOFT'S (IN)SECURITY UPDATES - Blaming the victim for broken software
Bill Gates and Microsoft have always promised us "easy" computing. And to a certain extent, they've done that, with the graphical user interface. Recently, however, we've all seen an increasing number of security issues with the Microsoft Windows platform (including Code Red, Slammer, Blaster, and the many other insecurities that we've had to deal with lately). Of course, these are a real problem given the damage that they can inflict on unsuspecting users. The problem is that Microsoft hasn't done a very good job of fixing these insecurities.
What is difficult to handle is the way that Microsoft and the media are presenting the security problems. You may have seen the headlines and text:
- "IT Users Botch Security Again...and again" -- ComputerWorld February 3, 2003
- "Users slow to adopt Web security" -- Oakland Tribune August 25, 2003
- "People should have been doing something with the patch...." -- eWeek February 3, 2003
The problem -- besides the fact that there are so many updates -- is that Microsoft's solution to fixing the problems is broken. I'm sure you've seen the "Windows Update" button on your Start menu that takes you to a Microsoft website to analyze your machine and optionally install whatever patches are required. You've probably also seen the little "balloon" message in your system tray that suggests you visit the Windows Update site to get your patches installed. There's even an option on newer Windows machines to automatically install all patches as they become available (dangerous).
Unfortunately Windows Update doesn't always work as expected. Furthermore, if you have more than one machine to deal with, you have to go through the process at each machine. It can be very time-consuming and you can still wind up with fixes improperly installed. Here are some examples.
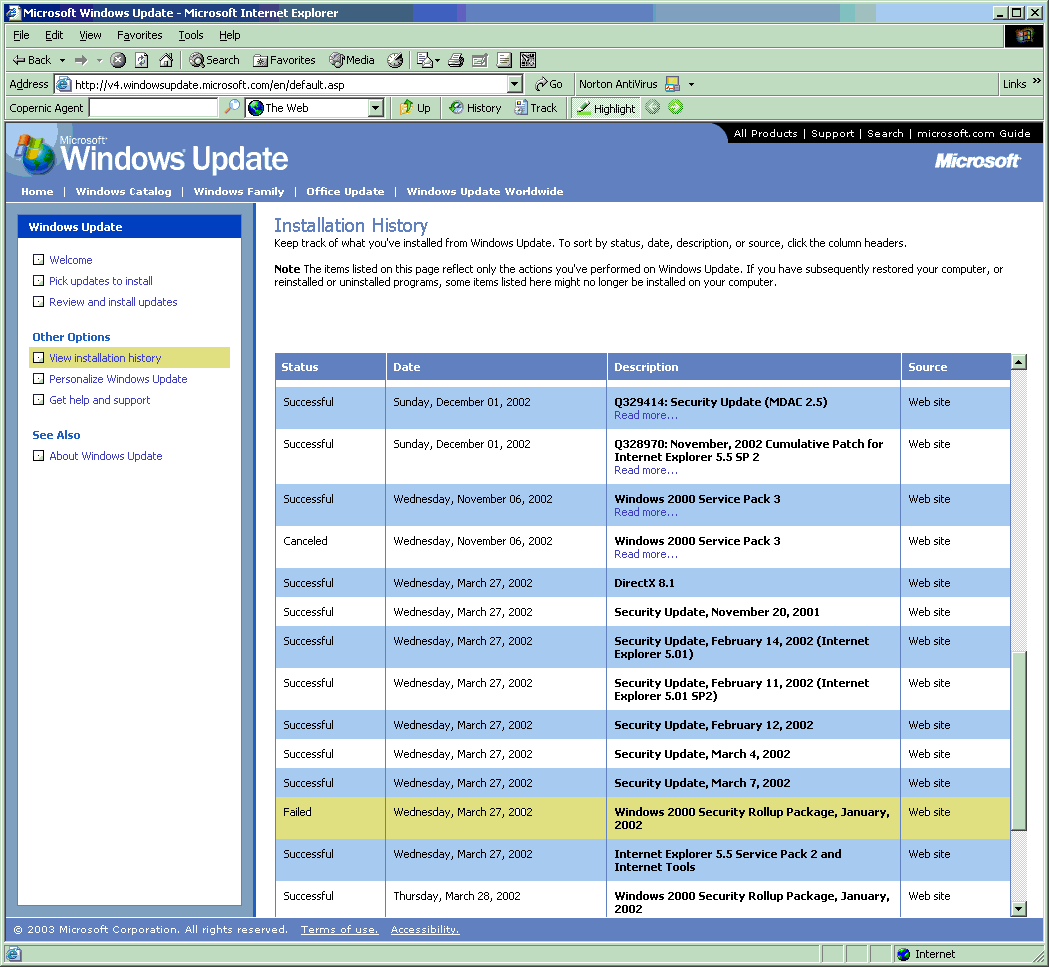
- Windows Update fails in the middle of installing updates for unknown reasons. The result is that you don't know if some, all, or none of the patches have been installed. Worse, there's no way that you can re-run those patches because Windows Updates won't consider those patches available for installation any longer -- even though it recognizes that the process failed. Here's the output from one of my machines that shows such a failure. Click on the image to see a larger picture.
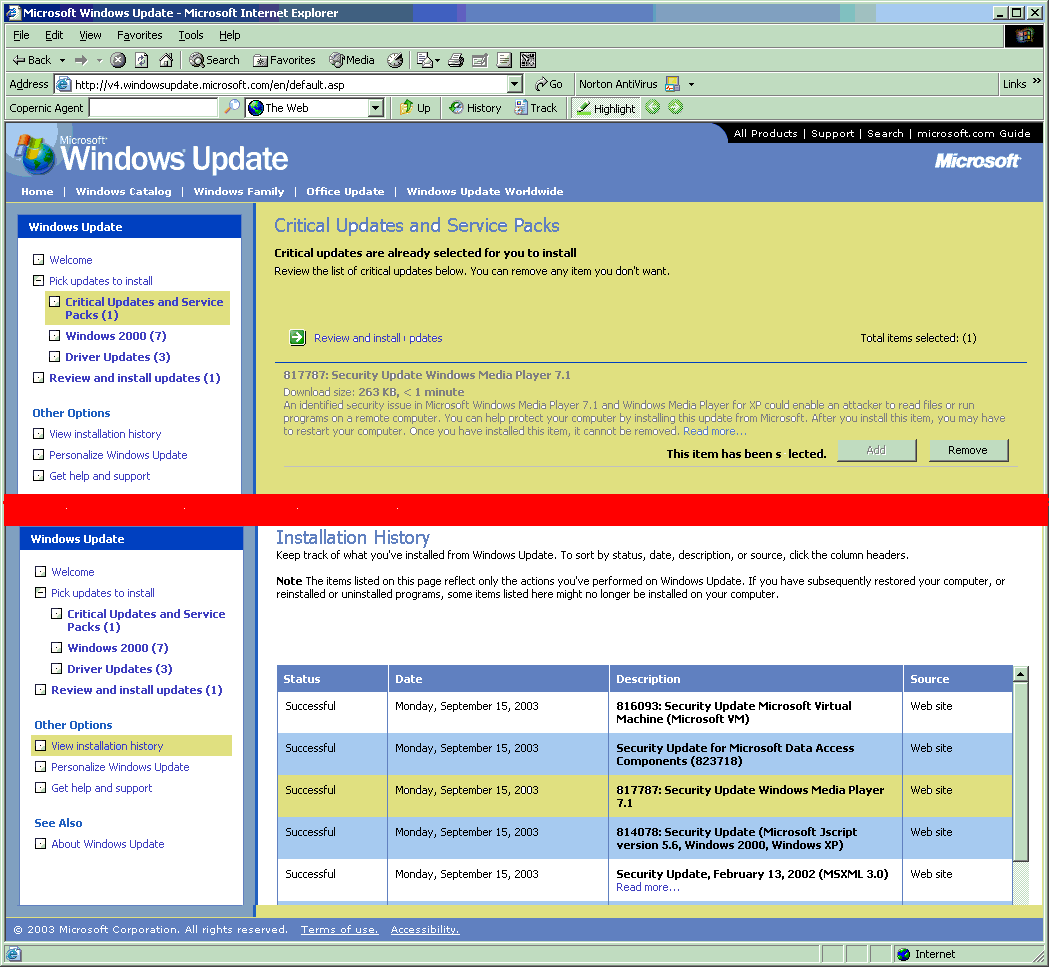
The yellow-highlighted section shows the failure. Once this happens, you're usually in for a session of finding the specific patch individually, downloading it yourself, and getting it installed. Definitely not as easy as Windows Update is supposed to be. If you attempted to install several updates at once, then you've got a number of individual installs to perform -- very time-consuming. - Windows Update advises you to install a patch that you've already installed. You install some patches, and then a patch that you've previously-installed shows up again as one that you should install. This happened recently on one of the machines that I maintain, and -- as a result -- I'm constantly being notified by my "helpful" Microsoft code that I have a critical patch to be installed. I could install it again, but there has obviously been some conflict between this patch and a subsequent patch, so what would be the result? I don't know. I could be "undoing" another patch and not realize it. Worse, re-installing the patch might cause other problems. Here's an example showing portions of two Windows Update screens: Patch #817787 has been successfully installed but shows as needing installation. There's no way that I know of to remove this message, so I have to keep ignoring it. (NOTE: the red horizontal bar separates the two different screens.) Click on the image to see a larger picture.
- Finally, you install one or more patches and literally break your machine. The software, not the hardware, I mean. I have one machine that completely stopped printing after installing a series of patches. I had to re-install the machine to get it working again and sometime later it broke again. Fortunately, this is an old machine that I only use for supporting my scanner, so it's not a real hassle for me. But it could have happened on a critically important machine.
An associate of mine and I agree -- the "Automatic Updates" feature (where the Windows Update program goes out and aotmatically installs your updates) is scary and is not to be trusted. It's bad enough to have the Update process break when you're monitoring it and have at least some idea of what's going on. It's another matter entirely when the Update programs goes out one night, finds a number of updates, and installs them without your knowledge. Who knows what could happen? On any given day, you could awake to find your machine unusable. Or, you could begin experiencing subtle problems that you can't pin down or resolve.
The point is that Microsoft's Update management schemes are radically flawed. Unfortunately, you have little choice if you want to stay somewhat protected, but approach with caution.
So... rather than it being the "fault" of the computer owners/users who didn't install the patches, I would submit that several other folks share the blame.
First of all, it is Microsoft's fault for turning out such buggy code in the first place. They've clearly focused more on churning out new features than they have been on making their systems secure. I also fault Microsoft for creating such an error-prone Windows Update tool: if everything works perfectly, then it's fine, but those of us who have been in the computer industry for some time know that nothing every works perfectly and that "real programmers" allow for errors when they are designing and coding systems.
Secondly, it is corporate management's fault for allowing such error-prone, high-maintenance systems to become the standard in their companies. The corporate world drives much of the demand for products; they could as well be driving the demand for secure products. As one IT professional remarked: "Why are we still using this stuff? If these problems were at this level for any other operating system, executives would have demanded that it be ripped out and replaced." ("Untrustworthy Computing", ComputerWorld, August 18, 2003, p20).
Finally, it is our fault for being complacent. We too readily accept the claims by Microsoft and others about products and services and don't examine the details to see what the real story is. When we get a lemon, we don't complain enough about the problems so that the vendors have to fix them.
WHAT TO DO? Install the patches, but take backups, work carefully, and keep your fingers crossed.
2. INSIDIOUS, MALICIOUS EMAIL - Be very, very careful
A couple of days ago I received an official-looking email that purported to be from Microsoft. It supposedly contained information about the latest updates and offered me a fix for some of the most recent security holes. My immediate reaction was to say: "Aha! It's finally time that Microsoft took a proactive position and got the word out to people." Fortunately, it quickly occurred to me that this is not the Microsoft Way and so I looked a little more closely at the email. You should never respond to an unsolicited email from Microsoft or anyone else that asks you to make changes to your system -- it's on the same level as someone asking you out of the blue for your social security number!
Take a look at the email as displayed on my system (a web-based email system that I use in addition to my Outlook email). Click on the image to see a larger picture.
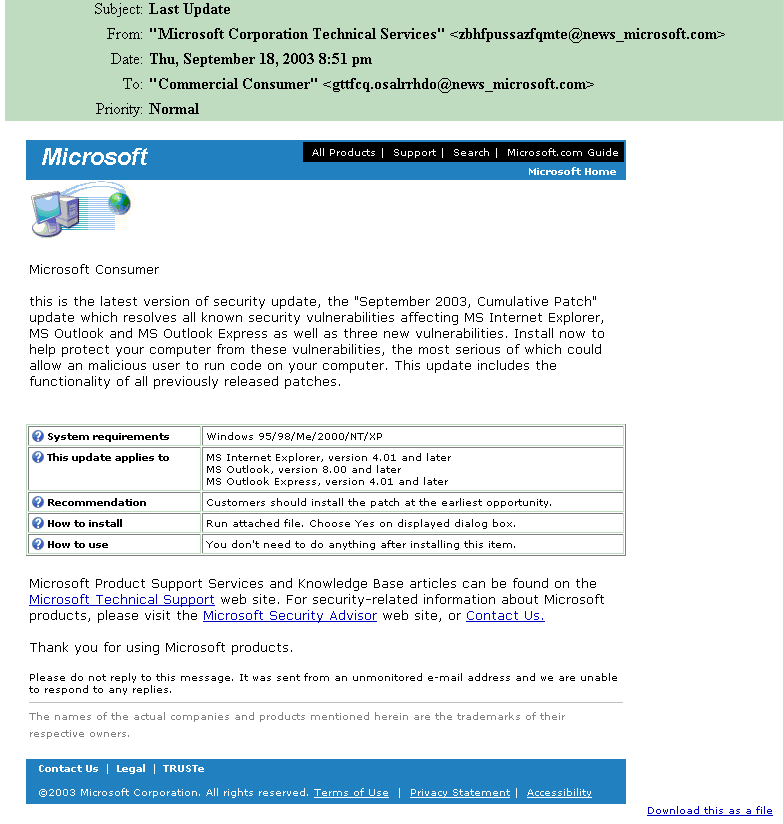
How many suspicious indicators can you see on this email? Once you've inspected it for yourself, check out the image that I've annotated with the items that raised my suspicion. I've highlighted the items that I thought were questionable. Click on the image to see a larger picture.
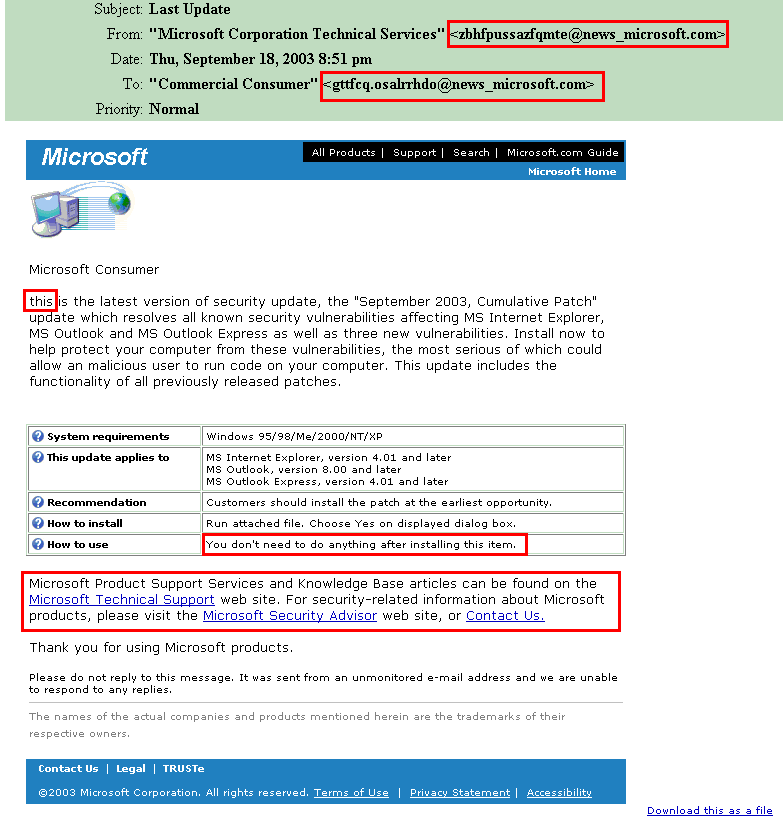
Some of them are red-flag warnings, like the "From" address that contains "zbhfpussaxfqmte" as the email address from which it was sent. Anytime I see something like that, I start to suspect that something is awry. The same thing goes for the "To" address. I started looking at the mesage itself, and it just didn't seem like something that Microsoft would have written. The text is VERY well spoofed, but the lack of capitalization in the first word, and the "You don't need to do anything after installing this item." added to my suspicions. Note that the links provided in the last highlighted paragraph are real links to the real Microsoft website, just to make it look more reasonable. On an obscure note, real domain names cannot have an underscore (_) in the name, so news_microsoft.com is immediately flagged as invalid.
Normally, I would have just deleted this, but I was curious so I examined the full headers (on a safe, isolated system) and this is what I saw. Click on the image to see a larger picture.
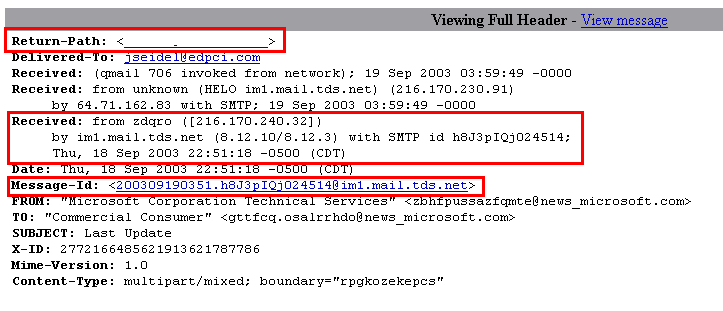
Again, the red boxes outline the suspicious items -- the most flagrant of which is the "Return-Path": it contains a definitely non-Microsoft address. I've erased the email address that I saw: I don't know if it's real or not, but I would presume that the culprits simply hi-jacked someone else's email, and I don't want to cause trouble for a potentially innocent person.
My sister apparently got hit by this or a similar virus and it caused havoc on her machine, and a similar virus has been discussed in eWeek magazine recently.
The eWeek virus email appears different than the one I received, but the hallmarks are the same: it has been carefully crafted to look as if it came from Microsoft, and it talks about a cumulutive patch that users need to install.
3. SECURITY CATCH-22 - Preventing re-infection while downloading patches
All this talk about security reminds me of the situation that we encountered when we delivered our youngest son to his new college campus apartment and went to set up his computer. They were very worried about the latest Microsoft vulnerability and had technicians visiting all the apartments as the kids moved in. They carried with them CDs for manually installing the patch -- only then would they allow the machines to log in to the network.
Every network connection was physically disabled (at least that was the theory) and would only be activated once the technican had seen the patch installed and confirmed that the machine was protected. Unfortunately, the network connection in my son's apartment was "hot", so when I logged on to download the patch, his computer got infected!
As it turns out, I have had a hardware firewall for some time. This device (from Netopia -- recommended) filters out or blocks unwanted traffic from the internet. Therefore, the situation described here is not an issue when I'm working from my home or office. The same is true of many corporate environment -- at least the larger companies.
But the school situation got me to thinking about how anyone else might handle this siutation for their personal machines -- i.e., those machines for which there's no corporate infrastructure that can provide patches on CD-ROM for safe installation and for which there's no firewall keeping you safe.
While wandering around the net recently, I found at least a partial answer, although it requires the willingness to do a little reconfiguring on your machine. This approach is described on an MIT Network Security page, and involves temporarily blocking all TCP (internet) traffic to your machine while you are connecting to the Windows Update site and downloading the latest patches. As the instructions note, make sure that you unblock the traffic once you've completed updating your computer.
I wish I had known about this before I went to school!
4. PERSONAL (IN)SECURITY EXPERIENCE - Letter to the editor
Here is the recent experience of a friend and business associate of mine:
Chuck McVey, VOLANT MANAGEMENT CONSULTING, writes:
A long time ago, I set up a browser home page on my system with URLs I often used. I have not used these URLs now for over two years but about 3 months ago, out of curiosity, I looked at a few of them.
Oops!!! Big mistake!
At least two are now porno sites and at least one of them was able to infect my system with a Trojan Horse virus. This happened despite the fact that I have, keep updated, and actively use several security systems. Additionally, these systems were unable to detect or remove the Trojan Horse; I had to do it manually. Other changes included the addition of icon shortcuts on my home page, registry changes, the addition of other shortcuts, a change of the default home page, and the addition of a program into my startup menu. FYI, this program, evidently downloaded from the sites before I was able to close the windows, was the first indication I had a problem. It masqueraded as an MS program in an operating system folder, and I would receive a message it was attempting to execute instructions outside its area.
Lessons learned include:
- When the sites began flashing up, my first inclination is to quickly click the "Close" button in the windows' upper right corner. WRONG!!! This simply sets off a series of other related sites and windows. Go to your system's Task Manager, usually accessed with the combination of <Control, Alt, Delete> and kill all open browser applications that are suspect.
- When you see the message that an application is attempting to execute outside its allocated area and requesting you to permit it to continue, do not be deceived if it looks like a part of your operating system.
- I need more protection than a software firewall and recently purchased a hardware firewall/router to augment my security.
- Just because a site has been innocuous -- even semiofficial -- in the past, do not expect that it will remain so.
FYI, the site that infected me used to be a travel site RE the Florida Keys The other site was an LA-area freeway-advisory system for CalTrans.
A last side note: Last week I received an E-Mail that looked real but just struck me as wrong. It was purportedly from MS and was supposed to contain an attachment to update MS Outlook and close a security vulnerability. That is NOT the way MS distributes system or application updates. A Virus can cause an E-Mail to look as if it originated with anyone, e.g., a family member. The technique is called "spoofing."
I have refrained from addressing basic or what I consider well-known aspects of security, but I must note it is advisable to keep your data files backed up and to keep current a system-repair disk.
Geeze! Chuck.
5. STATE OF THE ATTACKER'S 'ART' - Probing your website
To give you some idea of the level of insecurity on the internet these days, I took a quick look at the "weblogs" for my own (this) web site. The weblogs are where information is placed by the web server when something happens. The information here can be simple things such as lists of who visited the web site or it can be information about errors that ocurred. One of the errors that is logged on my system is information about which files someone tried to download but which were not there -- files "not found". This can be simply a case in which someone typed in a wrong name. It can also be a case where an automated program (called a 'robot' or 'web bot' or even 'spider') is scanning the internet to find something of interest.
Web bots are used by all the major search engines (they're often called 'spiders') to scan the internet and grab the information so that they can present it as the results of a search. These situations are pretty clear: you find that a program called "Googlebot/2.1 (http://www.googlebot.com/bot.html)" has accessed information on your system -- in fact, all the files on your system -- and you know that you've been scanned and that this information can be reported from a Google search. The other search engines do the same thing.
Web bots are also used by malicious users who are trying to find a way into your system through security holes that can be exploited through a website. These situations are usually indicated in your weblogs with an entry that says something like the following:
- script not found: .../cgi-bin/formmail.pl
script not found: .../cgi-bin/formmail.cgi
script not found: .../cgi-bin/Formmail.pl - file does not exist: .../scripts/..%5C%5C../winnt/system32/cmd.exe
- file does not exist: .../scripts/nsiislog.dll
- file does not exist: .../msadc/..<C0><AF>..<C0><AF>..<C0><AF>../winnt/system32/cmd.exe
Briefly, all of these are attempts by "someone" out there looking for a way to get into the system.
- Number 1 is an attempt to find a program called "formmail" that is known to be susceptible to being used as a "spam relay" -- that is, the program can be commandeered by an outside person to forward spam through your computer. (Note for my technical friends: The London Perl Mongers report that Security Focus identified the FormMail script as the third largest source of attacks in the first quarter of 2002. The London folks got together and wrote a secure replacment for the original FormMail script, which can be found at the nms site. There are other professional scripts there, too)
- Number 2 and Number 4 are both attempts to gain access to cmd.exe -- the DOS-like command program that is included in every Windows system -- so that an outside person can directly execute programs on your system.
- Number 3 is attempt to locate a program that is part of the Windows web server program and then be able to use it for their ends, effectively comandeering the system.
All these and a number of other attempts were made in the past 48 hours on my system -- and the same probes keep occurring, automatically and repeatedly.
If you leave your system open, someone out there will find it -- it's just a matter of time.
6. SECURITY CONCLUSIONS - A few (more) things to do to keep your computer safe
- Take computer security seriously:
- Be suspicious -- the bad guys (or "black hats" as they are often called) are getting better and better at what they do.
- Check things out before you install something on your machine that you haven't asked for. It may not be what it appears to be.
- Get a firewall for your system -- preferrably a hardware firewall rather than a software firewall. The hardware kind is more reliable.
- Keep your system up-to-date as much as you can... assuming that Microsoft's Windows Update doesn't sabotage you.
- Backup your system if you have data that you don't want to lose.
7. VOTING SYSTEMS - Letter to the editor
Last issue, I wrote about the possibility of voting fraud with the new computerized voting machines. Despite the protestations of Diebold, government officials, and experts, I remain unconvinced. Making computer systems secure is very difficult. It's just as wrong to swear that your systems are so secure that they can't be compromised (which leads to a false sense of security) as it is to throw up your hands and say it's too hard to secure systems so we won't really try.
One reader commented; here is his letter.
Mike Kanze, CORNERSTONE SERVICES, writes:
Thank you very much for sharing your thoughts concerning touch-screen voting and your recent experience with it in Alameda County. Much of the concern in your note centers about the problems flagged in the Johns Hopkins study. What caught my eye was the "Diebold-centeredness" of the study. For example there was no mention of problems encountered by Diebold's two major competitors, Election Systems & Software (ES&S) and Sequoia Voting Systems (Sequoia). The world of touch-screen voting machines is NOT the same as a "Diebold-only" world. The Santa Clara County approach - covered extensively over the last six months in the San José Mercury-News - has been thorough and has surfaced many of the same concerns as the Johns Hopkins study. The County and their preferred supplier (Sequoia) have been working proactively to address these concerns. I suspect that Santa Clara County will have the best iteration of this technology once it rolls out. The good news is that touch screen voting technology is not "rocket surgery". Current units have components that are very vanilla and "off the shelf". No esoteric CPUs or highly-proprietary hardware. The software is complex only to the extent that multiple language support dictates. So we are talking about units that are easy/cheap-to-make, easy-to-upgrade and easy-to-train-pollworkers-on. Nor is this technology "new" to voting. Several of the Florida "hanging chad" counties (Palm Beach County, for one) as well as California's own Riverside County have used touch screen voting systems in one or more recent elections, most with few to zero problems.
Some further thoughts: * The "people problem" is a much larger factor than the technology problem. A sampler:
- Until states - including California - require voter identification that positively and irrefutably recognizes an individual as a registered voter already on the rolls AND not having already voted (absentee, in another precinct, etc.) the possibility of fraud will remain an unacceptably large factor. Unfortunately the best means currently deployed is the very un-robust photo ID. Tomorrow, perhaps, some form of biometric ID will replace photo IDs.
- Today the voter registration process is another playground for potential electoral fraud. For example, "motor voter" is susceptible to abuse by high-quality fake IDs. The latest California drivers licenses and IDs are hard to fake, but not impossibly so. A visit to any college campus in search of high quality fake IDs will bear this out.
- Pollworker competence varies widely - and wildly. Your own experience is an excellent example. It was also a factor in many of the Florida counties having "hanging chad" problems during 2000. And don't forget - Mr. and Ms. John Q. Public will always be among the volunteer pollworkers in every precinct.
- Finally - while individual fraud is fairly easy to defend against, if some group is determined to compromise an election a way can be found no matter what the safeguards. Sometimes this is a deep-rooted part of the local culture, as in Chicago's reputation as a place where even the dead and the pets vote.
* The technology issues are largely - but not completely - "fixable". Some observations:
- Always remember that the current technology is first-generation. These units are the touch screen voting equipment equivalent of Apple IIs or IBM PCs. There will be many evolutionary changes the technology in the years ahead. o At least one manufacturer already provides a software upgrade that yields an auditable paper trail. New units have it as standard configuration. BTW, its hardware already had built-in thermal printers that allowed numerical tallies and the ability to lock-out the memory from any shenanigans.
- Any security system - including Smartcards - can be compromised. The trick is to make security so robust that the risk of individual fraud is so small as to be inconsequential. For Smartcards, the countermeasure is strict accountability for each card, plus perhaps some strongly-encrypted identifier. Not 100% foolproof to be sure, but a step in the right direction. (BTW, the need for "strict accountability" leads us back to limitations imposed by the "people problem" above.) One next-generation security proposal would require biometric identification by the voting machine itself, bypassing the need for Smartcards - or the possibility of any kind of human error or fraud in the registered voter validation process.
- Designing in - or maintaining - simplicity and robustness reduces the likelihood that pollworkers like Mr. or Ms. Public may "do it" wrong / backwards / etc. Unfortunately the pressure lies in the opposite direction, from both competitive product developments and from jurisdictions demanding ever more complex "whistles and bells". Succumbing to this pressure also risks over-complicating the (today) very simple ATM-like experience of touch screen voting.
- Battery backup for any touch screen voting technology is a must, especially in jurisdictions "served" by PG&E. Most manufacturers have this, either as standard equipment or as an option.
Cheers! Mike
** FEEDBACK -- Comments, please [2007-05-27: Disabled, due to spambots]
As always, comments are welcome. Use the form below to send them to me. If you tried to use the email form I included in my last email, my apologies -- it was broken. This one works :)
Thank you, Mike and Chuck for your comments.
Enjoy, everyone!
...jon
_
![]()
edp consulting, inc.
3373 Guido Street
Oakland, CA 94602
Tel: 510-530-6314
Fax: 510-531-1522
Contact Us
![]()
.
